Merchants use IP addresses to retrieve their customers’ geolocation information in order to provide a better user experience. Proxies are useful in protecting customers’ identities. While proxies have legitimate uses, a lot of people tend to abuse them to gain access to services or products.
Fraudsters frequently used proxies to perform fraudulent activities like credit card fraud. As a result, merchants pay the price. Therefore, measures should be taken before it is too late.
What is a fraudulent IP
Before we jump into how to catch proxy IPs, there is a need to know what is a proxy IP. As we know, IP addresses are unique identifiers assigned to devices connected to the internet. Proxies which act as an intermediary between a user’s device and the internet are often used by fraudsters to hide their real identities and then perform fraudulent activities like scamming, phishing and so on. These IPs are fraudulent.
How do fraudsters use proxies
Credit card fraud example
Fraudster can use proxy servers to display various IP addresses for each transaction. How do fraudsters use proxies to commit credit card frauds? Let’s look at this example.
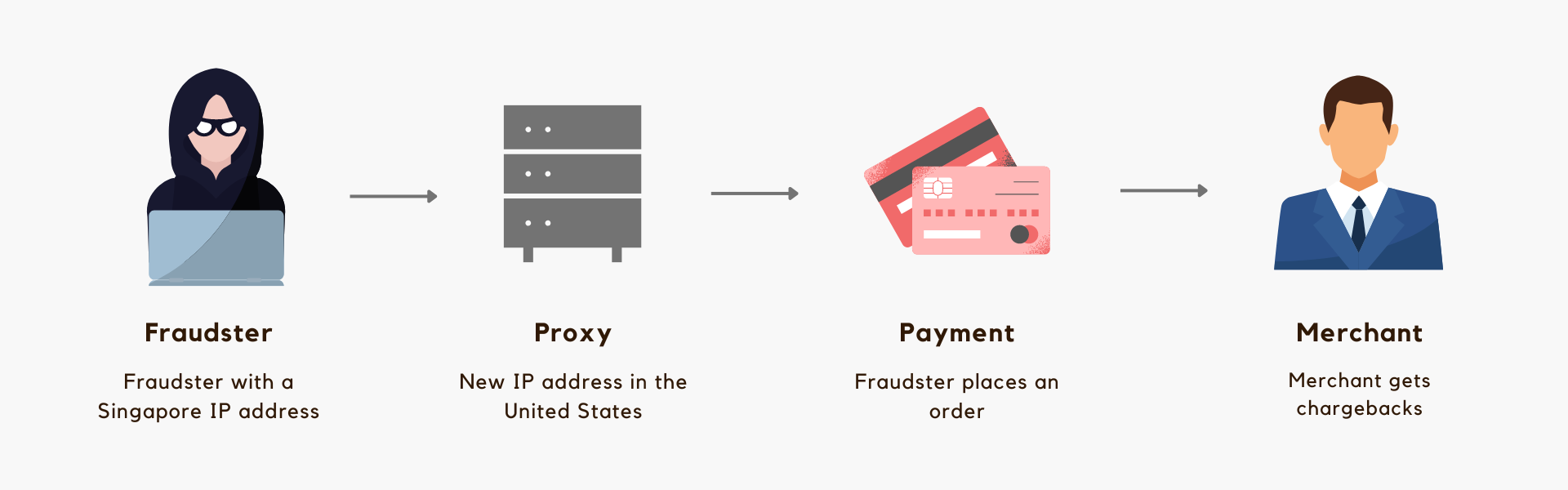
The fraudster, who is from the Singapore, uses a proxy to show his location in the United States. Then, he places an order with a stolen credit card. As a result, the merchant gets hit with chargebacks.
Fraudsters are good at mimicking real users and try to trick merchants with their fraudulent IPs. They use stolen credit card information to make purchases online or transfer funds to their own accounts. Merchants will think that it is a real order originates from a real person but will end up with chargebacks in the end.
Web scraping example
Web scrapers can use proxies to perform web scraping in a more efficient and effective manner. How do scrappers use proxies to commit website scrapping? Let’s look at this example.
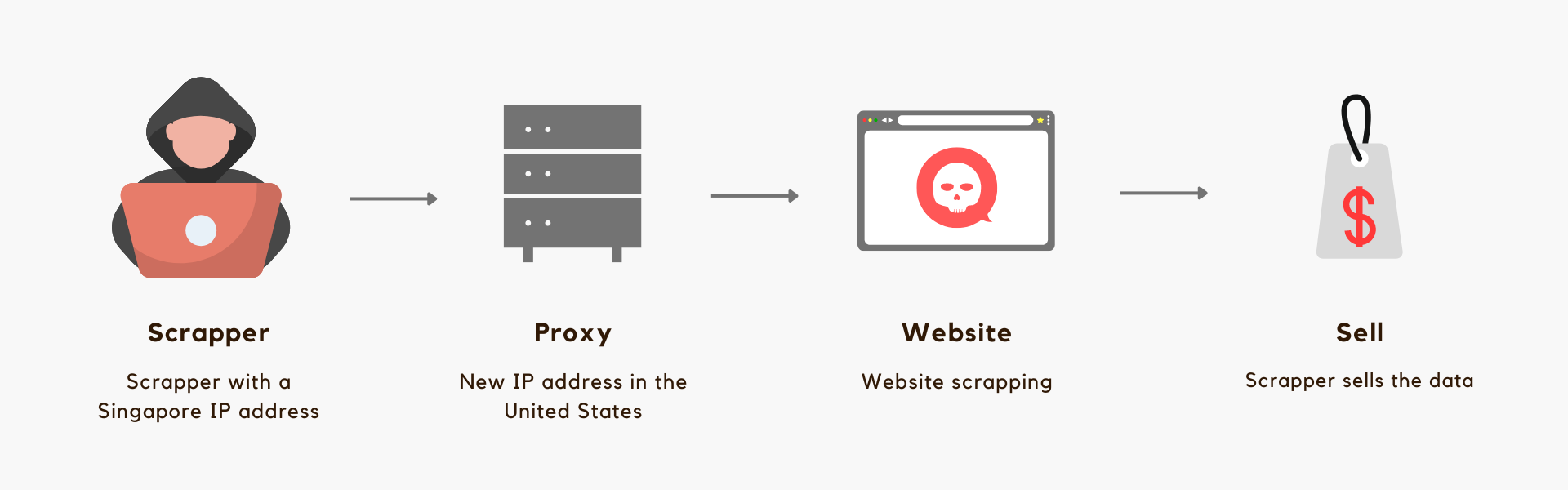
The scrapper, who is from the Singapore, uses a proxy to mask his actual location. By using proxy, he appears in the United States rather than in Singapore. Then, he performs scraping of websites and lastly sells the data collected.
By using multiple proxies, web scrappers can access website contents and gather data more quickly without being detected. They can also bypass IP geolocation blocking by connecting to proxy servers. As a result, sensitive information, pricing data, and other data are exposed to unauthorized users and cause losses.
How do fraudsters hide their IP addresses
Fraudsters use different proxy types to increase their chances of avoiding detection. You can read further on how different proxy types can affect your business.
Anonymizing VPN services
- Common way to hide IP address.
- For the purpose of hiding real IP address location.
- Makes it difficult to track fraudsters’ online activities.
Tor exit nodes
- For those who wish to maintain anonymity.
- Exit nodes are public.
Data center proxies
- Hosted on servers in data centers.
- Often use for web scraping, account creation.
Public proxies
- Make connection requests on a user’s behalf.
- Can be configured by the administrator to listen on some specified port.
- Have limited functionality compared to VPNs.
Residential proxies
- Comes from a regular Internet Service Provider (ISP).
- Associated with real residential internet connections.
- Hard to differentiate a legitimate user from a proxy server.
- Fraudsters use it to mimic the behavior of genuine users.
Botnet
- Controlled remotely by a command & control (C&C) server.
- In a credential stuffing attack, the bots will attempt to log in to your e-commerce site.
- Potential for many customer account takeovers.
How to detect fraudulent IPs
By using IP2Proxy Proxy Detection API, online merchants or service providers can detect whenever someone is using a proxy server IP to visit their websites. We can detect different types of proxies used by fraudsters like VPN, DCH, RES and so on.
Once you have determined these are proxy IPs, you can monitor their activities to ascertain if they are committing fraud. If fraudulent actions are taking place, these are fraudulent IPs.
After that, you can take action to mitigate the fraud.
Benefits of the IP2Proxy API
- Real-time proxy detection API.
- Secures all data via SSL encryption.
- Different granularity of geolocation data available.
Result of the IP2Proxy Proxy Detection API
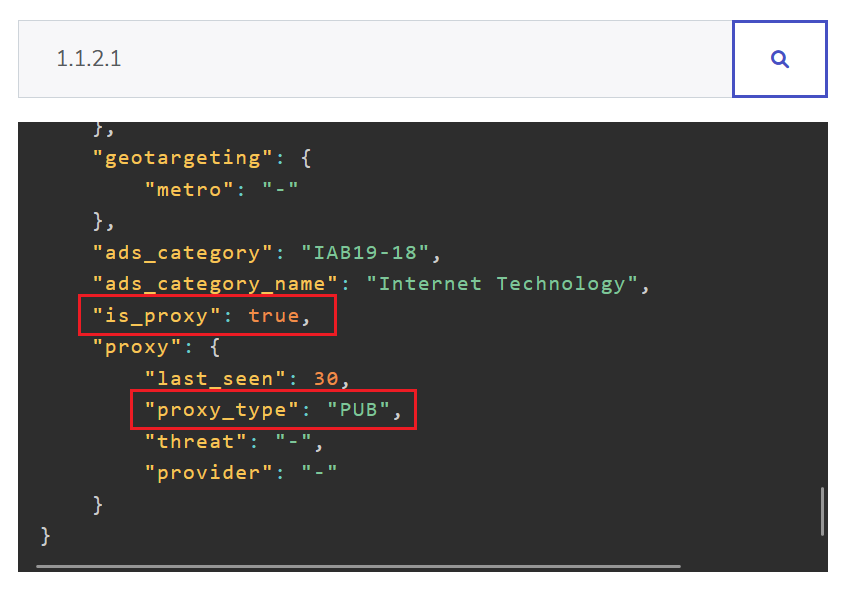
This is the result of IP2Proxy API. Based on the result below, we detected that this particular IP is a proxy and its proxy type is PUB. You can monitor this IP activities closely before flagging it as fraudulent. If any suspicious activities detected, just mark it as fraudulent IPs.
Conclusion
Detecting fraudulent IPs is a must to prevent fraud losses. By using the IP2Proxy API, you can protect your site and web application by filtering detected fraudulent IPs. Try out the IP2Proxy API today.
Bonus Tip: If you require a full-featured fraud prevention system to protect your online store, do consider the FraudLabs Pro Fraud Prevention service.
