
Intro
Dart is a client-optimized, object-oriented programming language developed by Google for building fast apps on multiple platforms, including mobile, desktop, web, and server-side applications. It is best known as the language behind Flutter, Google’s UI toolkit for creating cross-platform applications. Dart features C-style syntax, modern capabilities like null safety and async-await, and the ability to compile to different machine code and JavaScript targets.
In this article, we’ll show how to use the IP2Proxy Dart package in a Dart command line (CLI) project to easily query the IP2Proxy BIN files to retrieve proxy data for a list of IP addresses. Our example will be using Debian 13 so some of the steps will be specific for that platform.
Pre-requisites
First, install Dart if you don’t have it installed on your system. Refer to https://dart.dev/get-dart for the installation steps specific to your system. In addition to that, you’ll also need the IP2Proxy PX12 BIN database files that contains the proxy data. You can download the BIN file from either of the below:
Commercial BIN files: https://www.ip2location.com
Free LITE BIN files: https://lite.ip2location.com
Download the zipped file and extract the BIN file to a folder of your choosing. For our case, we are storing the BIN file path as /home/admin/data/IP2PROXY-PX12.BIN so that’s what we’ll use later.
Create a new Dart console project
Navigate to the folder where you want to create the new project. In our case, it’s dartarticle.
Next, run the below command to create an initial Dart console project.
dart create -t console ip2proxy_cli
Then, navigate to the newly created folder.
cd ip2proxy_cli
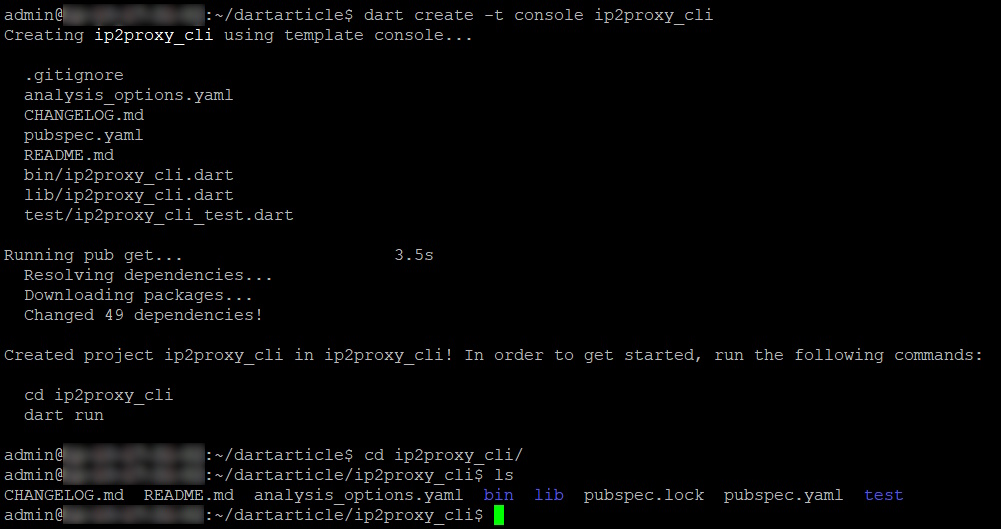
This creates a small CLI app with bin/ip2proxy_cli.dart as the entrypoint.
Include the IP2Proxy Dart as a dependency
Check for the latest version of the IP2Proxy Dart package at https://pub.dev/packages/ip2proxy/install and modify the code below for that version. We are also using the args package for specifying the command line parameters.
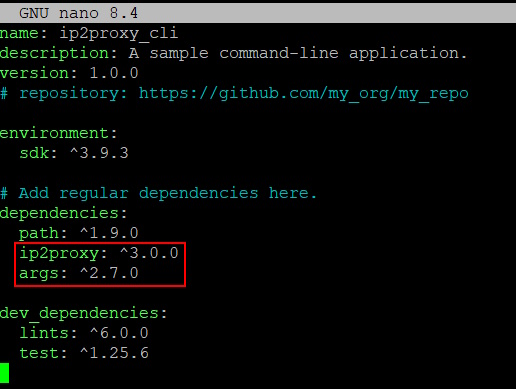
Edit the pubspec.yaml and add the below under the dependencies section:
ip2proxy: ^3.0.0 args: ^2.7.0
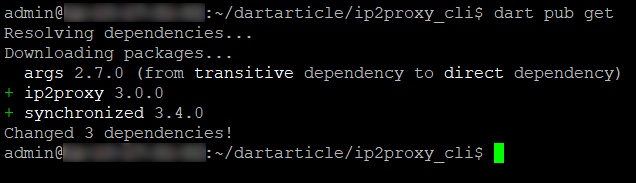
Save the file and run the command below to fetch the dependencies.
dart pub get
Implement the command line codes
Edit bin/ip2proxy_cli.dart and replace the existing codes with the codes below.
import 'dart:convert';
import 'dart:io';
import 'package:args/args.dart';
import 'package:ip2proxy/ip2proxy.dart';
Future<void> main(List<String> arguments) async {
final parser = ArgParser()
..addOption('db', abbr: 'd', help: 'Path to IP2Proxy BIN database')
..addOption('input', abbr: 'i', help: 'Path to file containing IP addresses (or omit for stdin)');
final results = parser.parse(arguments);
final dbFile = results['db'] ?? 'IP2PROXY-LITE-PX1.BIN';
final inputFile = results['input'] ?? '';
final ipx = IP2Proxy(databasePath: dbFile);
Stream<List<int>> inputStream;
if (inputFile.isNotEmpty) {
final file = File(inputFile);
if (await file.exists()) {
inputStream = file.openRead();
} else {
stderr.writeln('Error: File not found: $inputFile');
exit(1);
}
} else {
inputStream = stdin;
}
// Print CSV header (quoted)
print([
"ipAddress",
"isProxy",
"proxyType",
"countryShort",
"countryLong",
"region",
"city",
"isp",
"domain",
"usageType",
"asn",
"as",
"lastSeen",
"threat",
"provider",
"fraudScore"
].map(_csvEscape).join(','));
// Process line by line
await for (final ip in inputStream.transform(utf8.decoder).transform(LineSplitter())) {
final result = await ipx.getAll(ip.trim());
print([
result.ipAddress,
result.isProxy,
result.proxyType,
result.countryShort,
result.countryLong,
result.region,
result.city,
result.isp,
result.domain,
result.usageType,
result.asn,
result.asName,
result.lastSeen,
result.threat,
result.provider,
result.fraudScore
].map((e) => _csvEscape(e.toString())).join(','));
}
}
/// Escapes values for CSV (wraps in quotes if needed, doubles inner quotes)
String _csvEscape(String s) {
// Always quote, even if not strictly required
return '"${s.replaceAll('"', '""')}"';
}
User can optionally specify the location of the BIN file using the -d flag. If not specified, the code will look for IP2PROXY-LITE-PX1.BIN instead. Using the optional -i flag, user can make the code read IP addresses from a text file. In the input file, there should be 1 IP address per line. If the input file is not specified, the code will assume STDIN as the input.
Test the code
Let’s test the code and make sure everything is working.
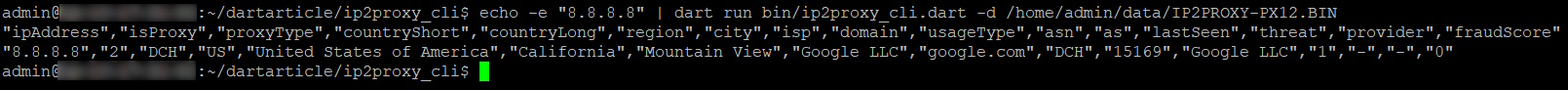
Use the command below to test the code.
echo -e "8.8.8.8" | dart run bin/ip2proxy_cli.dart -d /home/admin/data/IP2PROXY-PX12.BIN
You’ll see the results below.
"ipAddress","isProxy","proxyType","countryShort","countryLong","region","city","isp","domain","usageType","asn","as","lastSeen","threat","provider","fraudScore" "8.8.8.8","2","DCH","US","United States of America","California","Mountain View","Google LLC","google.com","DCH","15169","Google LLC","1","-","-","0"
Compile into executable binary
To make it easier to distribute to other Linux users, we can go an extra step and compile it into a native executable binary.
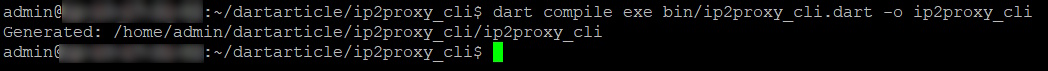
Run the below command in the root of your project folder to compile the code.
dart compile exe bin/ip2proxy_cli.dart -o ip2proxy_cli
Run the executable to get your proxy results
Run the executable to get your proxy data similar to our testing command, with just a slight difference. Let’s try piping 2 IP addresses to the program and see.
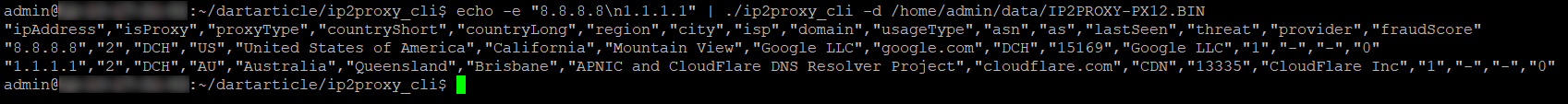
echo -e "8.8.8.8\n1.1.1.1" | ./ip2proxy_cli -d /home/admin/data/IP2PROXY-PX12.BIN
You should see the results below.
"ipAddress","isProxy","proxyType","countryShort","countryLong","region","city","isp","domain","usageType","asn","as","lastSeen","threat","provider","fraudScore" "8.8.8.8","2","DCH","US","United States of America","California","Mountain View","Google LLC","google.com","DCH","15169","Google LLC","1","-","-","0" "1.1.1.1","2","DCH","AU","Australia","Queensland","Brisbane","APNIC and CloudFlare DNS Resolver Project","cloudflare.com","CDN","13335","CloudFlare Inc","1","-","-","0"
Conclusion
We’ve shown a simple example above for piping in the IP address to query for the proxy data. The code above also supports reading the IP addresses from a text file using the -i flag when calling the executable. Give it a try for yourself and you’ll soon find this to be a useful tool to have for a quick check for proxy servers in your IP address list. This feature is especially handy for system administrators who need to analyze web server logs or other log files.
DISCOVER THE POWER OF IP GEOLOCATION
Find a solution that fits.
DISCOVER THE POWER OF IP GEOLOCATION
Find a solution that fits.
