
IP2Location.io IP Access List provides an additional layer of security by allowing you to restrict API endpoint access to specific IP addresses or ranges. This ensures that only trusted sources can interact with IP2Location.io Geolocation API services with your API key.
Unauthorized API access leads to both data breaches and resource misuse and system-wide downtimes. The implementation of IP access control enables you to decrease system vulnerabilities by establishing the list of trusted IP addresses. The API verifies requests coming from trusted networks only, as all other requests will be automatically blocked.
Please note that this feature is only available for Starter Plan onward.
Configure IP Access List
Setting up IP Access List is simple and intuitive.
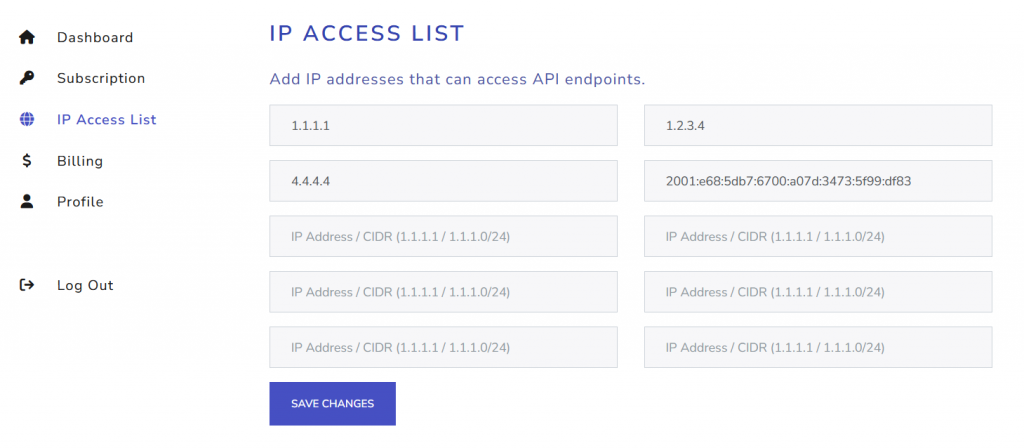
- Go to IP2Location.io dashboard and select IP Access List from the side menu.
- Add individual IP addresses or ranges to your whitelist. You can enter up to 10 IP addresses or CIDR ranges.
- Press “Save Changes” button to apply the changes. It may take up to 5 minutes for the changes to propagate to all API nodes.
Below is the example screenshot of the settings.
Note: If you want to allow the API to be accessed from any IP address without restrictions, remove all IP addresses from the List
Error Message for API Calls Blocked by IP Access List
When the IP access is restricted, you will get the following response with a status code of 403.
{
"error": {
"error_code": 10005,
"error_message": "Your IP address has been blocked from accessing this service."
}
}
Best Practices for IP Access Control
Only whitelist the IP addresses that are essential for accessing the API, such as those belonging to your company’s servers, trusted partners, or specific client devices. This minimizes exposure to unauthorized access and reduces the risk of security breaches.
Regularly reviewing and updating the access list is crucial to align with any changes in your operational needs, ensuring that outdated or unnecessary IPs do not remain on the list. Additionally, monitoring API access logs allows you to detect any unauthorized attempts and adjust security settings accordingly.
THE POWER OF IP GEOLOCATION API
Find a solution that help in your business.
