
What is a scanner?
The scanner here does NOT refer to the electrical device that helps you to digitize any physical documents, images or objects. Instead, it means any kind of software that is used to scan for any vulnerabilities or system information. The main purpose of the scanner is to help discover any potential vulnerabilities, malware or network issues within a system.
Scanners can be classified into a few types depending on the usage, such as:
- Network scanner – detect information like connected devices, open ports and running service on a network.
- Web application scanner – analyze a web application for any security vulnerabilities or performance issues.
- Database scanner – analyze the database for any soft spot that is potentially open to malicious attacks.
IT administrators or security professionals often rely on scanners to perform a security audit for various systems such as servers, networks and other online services.
Why do people blacklist the scanner?
Although the scanner was initially designed with good intent, however some people had misused it to carry out malicious activities. Since the scanner is able to find potential vulnerabilities in the system, the attackers tend to abuse the scanner as much as possible. As a result, many network administrators had to block the scanners from trying to access and monitor the systems.
Should I whitelist the scanner?
As mentioned above, scanners were blocked due to the bad actors trying to find any weakness in the IT infrastructure so they can wreak havoc for financial or political gains. However, there are some circumstances that might necessitate the unblocking of the scanners.
Typically, it happens when you hire someone to scan for any underlying vulnerability in your system. To make sure the scanning process runs smoothly, he or she will request you to whitelist a certain scanner.
The request is to ensure that the scanner will not be blocked by any security mechanisms in your system, for example the firewall. You may ask, should I add a particular scanner into the whitelist?
Basically, there are few scenarios where you should do so, which are:
When you know it is a trusted scanner
Means that this scanner is a widely known and reliable one, and also known as not coming from the attacker. This could be scanners developed by some famous anti-virus software company, or any notable tech companies. E.g., Palo Alto Expanse.
When you have scheduled the scan
You will be required to whitelist the scanner if you have scheduled a scan from a 3rd party. They will send you the user agent that they are going to use, or their scanner IP, to differentiate from the attackers. They will also let you know their schedule for running the scans.
If the scanner is actually a part of your system
In some cases, organizations might have integrated the scanners into their internal systems. They may use the integrated scanners for network monitoring, updates checking and patching, and any other purposes. Hence, it is advisable to not block them if it’s from internal services.
Pay attention when you perform a whitelisting
As we mentioned before, there are some reasons why people tend to block the scanner. If you didn’t look carefully when whitelisting a scanner, you may:
Accidentally whitelisted scanner from untrusted source
It is dangerous when you don’t know where the scanner is coming from, or if it is trustworthy. Unverified scanners may introduce more security risks to your system, resulting in more vulnerabilities to your system.
Exposing unpatched exploits to the attacker
To avoid being blocked by the firewall, attackers will camouflage their scanner as a valid one. Failure in identifying these will unintentionally “invite” the attackers to attack your system, and may cause disaster.
Best practices in whitelisting scanners
Now we know why we should whitelist the scanner, and what are the consequences of not properly handling the scanner. You might be asking yourself: how can I make sure I can properly whitelist the scanner?
There are some general guidelines that you can follow when whitelisting the scanner:
Evaluate the source
Remember, never whitelist a scanner if you don’t know where it comes from or what it is trying to do here. Only whitelist those scanners that you have a clear understanding on.
Monitor the scanner
After you’ve whitelisted the scanner, your job does not end there. You will have to monitor them on a regular basis. For example, you might need to review the access log for your web server once every few days to make sure it is performing as intended.
Review the whitelist
Apart from monitoring the scanner’s activity, you will also need to perform a regular review on the whitelist. This is to make sure that the scanner list in the whitelist is up to date. You can also make sure that you have only whitelisted necessary scanners.
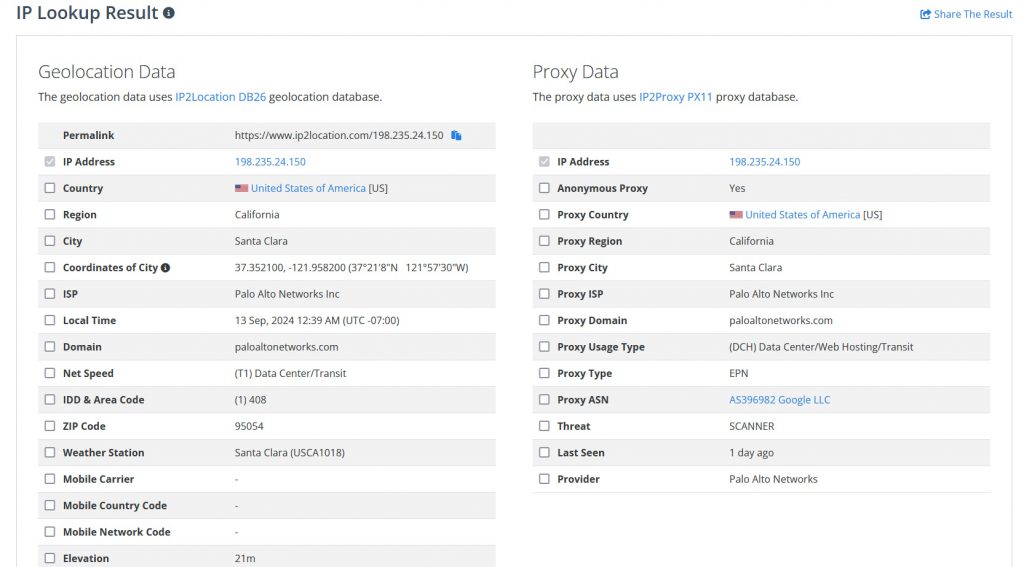
Check the geolocation information of the scanner’s IP address
To make sure that the scanners actually belong to the proclaimed organization, you can use the IP2Location demo page to lookup for the organization and proxy information of the scanner’s IP address. This is to make sure that the owner of the scanners are not disguising their identity.
Conclusion
Scanners are important tools that not only help you to defend your system but also help to make sure your system is free from any possible security or performance issues. However, system administrators must proceed with caution when whitelisting the scanners. Implementing best practices around whitelisting ensures a balanced and secure approach.
THE POWER OF IP GEOLOCATION
Find a solution that fits.
